Navigation
Report Format ll-int-win¶
This analysis report format applies to a dynamic analysis run on a Microsoft Windows platform.
In addition to the report fields that all report formats share (see Analysis Report Format), the report contains a number of different fields with details about the analysis run.
Report contents
- remarks: (optional).
Type: Dictionary.
- info (optional).
Type: List of strings.
Example: “Text1”,”Text2”.
A list of information strings concerning the analysis run.
- warning (optional).
Type: List of strings.
Example: “Text1”,”Text2”.
A list of warning strings concerning the analysis run.
- overview.
Type: Dictionary.
- analysis_engine.
Type: String.
Example: “LLama - WindowsXP”.
Name of the analysis engine used for generating the result.
- analysis_engine_version.
Type: String.
Example: “1.2.4”.
Version of the analysis engine used for generating the result.
- analysis_start.
Type: Date-Time.
Example: “2013-10-05 14:21:01.928894”.
Start timestamp of the analysis run.
- analysis_end.
Type: Date-Time.
Example: “2013-10-05 14:22:02.935794”.
End timestamp of the analysis run.
- analysis_subjects.
Type: List of analysis subjects; see Windows Analysis Subject Format.
A list of programs monitored during the analysis run.
- analysis_metadata: (optional).
Type: List of analysis metadata; see Windows Analysis Metadata Format.
A list of artifacts generated during the analysis run. See
get_result_artifact()for retrieving this metadata.
- randomized_registry_values: (optional).
Type: List of registry keys; see registry_reads.
A list of Microsoft Windows Registry values that the analysis engine randomized during the analysis run to avoid detection by the analysis subject. For the format of each value, refer to registry_reads.
- url_summary: (optional).
Type: List of strings.
Example: “http://www.example1.com”,”http://www.example2.com”.
Network summary of contacted URLs during analysis run.
Windows Analysis Subject Format¶
The analysis engine will monitor all analysis subjects, such as the originally started program and all child processes or processes that a monitored program interacts with, and then list any security relevant data.
This type extends the Analysis Subject Format type with additional information on Windows analysis subjects.
Analysis subject contents
- overview.
Type: Dictionary.
Overview of the analysis subject. In addition to the base format contents, the following elements are extracted:
- process.
Type: Process; see Windows Process.
Information on the Windows process.
- ext_info: (optional).
Type: File-Info; see Static File Information.
Static information on the process image.
- console_output: (optional).
Type: Dictionary.
Console output of the program.
- stdout: (optional).
Type: String.
Example: “text written to stdout”.
Program output written to default console.
- stderr: (optional).
Type: String.
Example: “text written to error console”.
Program output written to error console.
- opened_windows: (optional).
Type: List of GUI-windows; see below.
A list of GUI windows opened by the analysis subject.
- title:
Type: String.
Example: “Documents and Settings”.
Window title content.
- text:
Type: String.
Example: “FolderView”.
Window text content.
- loaded_libraries: (optional).
Type: List of libraries; see below.
List of library files loaded by the analysis subject.
- filename:
Type: String.
Example: “C:\windows\syswow64\ole32.dll”.
Path to the library loaded by the analysis subject.
- registry_reads: (optional).
Type: List of registry keys; see below.
A list of registry keys read by the analysis subject.
- key.
Type: String.
Example: “HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\DRIVERS32”.
A registry key.
- value: (optional).
Type: String.
Example: “wave9”.
A registry value.
- data: (optional).
Type: String or Integer.
Example: 1, “mso.dll”.
A data of registry value.
- registry_writes: (optional).
Type: List of registry keys; see registry_reads.
A list of registry keys written by the analysis subject.
- registry_deletions: (optional).
Type: List of registry keys; see registry_reads.
A list of registry keys deleted by the analysis subject.
- file_reads: (optional).
Type: List of files; see below.
A list of files read by the analysis subject
- filename.
Type: String.
Example: “desktop.ini”.
A file name. Could be absolute or relative path.
- abs_path: (optional).
Type: String.
Example: “C:\Users\desktop.ini”.
An absolute path the file.
- ext_info: (optional).
Type: File-Info; see Static File Information.
Static file information.
- file_writes: (optional).
Type: List of files; see file_reads.
A list of files written by the analysis subject.
- file_deletes: (optional).
Type: List of files; see file_reads.
A list of files deleted by the analysis subject.
- file_hardlinks: (optional).
Type: List of files; see file_reads.
A list of files hardlinked by the analysis subject.
- file_renames: (optional).
Type: List of files; see file_reads.
A list of files renamed by the analysis subject.
- file_queries: (optional).
Type: List of files; see file_reads.
A dictionary of files which status was being queried by the analysis subject. Key - file object. Value - status (int value)
- file_searches: (optional).
Type: List of strings.
A list of files searched for by the analysis subject.
- process_interactions: (optional).
Type: List of process-interactions; see below.
A list of processes the analysis subject interacts with.
In addition to the fields of type Windows Process, each element contains the operation(s) performed:
- operations:
Type: List of strings.
Example: “create_thread”,”write_mem”.
The type of operations performed on the remote process. Possible values are:
“create_process”: Create a process.
“terminate_process”: Terminate a process.
“create_thread”: Create a thread.
“terminate_thread”: Terminate a thread.
“read_mem”: Read from the process memory.
“write_mem”: Write to the process memory.
- mutex_creates: (optional).
Type: List of mutexes; see below.
A list of mutex synchronization objects created by the analysis subject.
- mutex_name:
Type: String.
Example: “Mutex1”.
Name of the mutex synchronization object.
- mutex_opens: (optional).
Type: List of mutexes; see mutex_creates.
A list of mutex synchronization objects opened by the analysis subject.
- raised_exceptions: (optional).
Type: List of exceptions; see below.
A list of exceptions raised by the analysis subject.
- addr: (optional).
Type: Hexadecimal number.
Example: 0x7c832297.
Instruction address raising the exception.
- code: (optional).
Type: Hexadecimal number.
Example: 0xc0000005.
Microsoft Windows exception code.
- name: (optional).
Type: String.
Example: “STATUS_ACCESS_VIOLATION”.
Microsoft Windows exception name.
- exception_name: (optional).
Type: String.
Example: “Exception 0xc0000005 (STATUS_ACCESS_VIOLATION) at 0x7c832297 (subject_id: 2)”.
Full exception information.
- exception_count: (optional).
Type: Integer.
Example: 1.
Number of exception occurrences.
- idt_hooks: (optional).
Type: List of the modified IDT entries; see below.
A list of the modified by the analysis subject IDT entries.
- vector: (optional).
Type: Integer number.
Example: 113.
An interruption number.
- isr_address: (optional).
Type: Hexadecimal number.
Example: 0xfffff800019fc710.
An original virtual address of the ISR (Interrupt Service Routines).
- new_isr_address: (optional).
Type: Hexadecimal number.
Example: 0xfffff880041f1b9d.
A new virtual address of the ISR (Interrupt Service Routines).
- isr_module_name: (optional).
Type: String.
Example: “c:\windows\system32\ntkrnlmp.exe”.
A module which contains the original ISR (Interrupt Service Routines).
- new_isr_module_name: (optional).
Type: String.
Example: “c:\windows\system32\hellodrv.sys”.
A module which contains a new ISR (Interrupt Service Routines).
- modification_sources: (optional).
Type: List of the sources of the IDT modifications; see modification_sources.
- ssdt_hooks: (optional).
Type: List of the modified SSDT or Shadow SSDT entries; see below.
A list of the modified by the analysis subject SSDT/Shadow SSDT entries.
- service_index: (optional).
Type: Hexadecimal number.
Example: 0x30.
A service index in the service table.
- service_address: (optional).
Type: Hexadecimal number.
Example: 0x8057fc60.
An original address of the service function.
- new_service_address: (optional).
Type: Hexadecimal number.
Example: 0xf7a574b1.
A new address of the service function.
- service_module_name: (optional).
Type: String.
Example: “c:\windows\system32\ntkrnlmp.exe”.
An original module which contains the service function.
- new_service_module_name: (optional).
Type: String.
Example: “c:\windows\system32\ntkrnlmp.exe”.
A new module which contains the service function.
- service_function_name: (optional).
Type: String.
Example: “NtCreateProcessEx”.
A name of the modified service function.
- table_name: (optional).
Type: String.
Example: “system service table”.
A name of the system table.
- modification_sources: (optional).
Type: List of the sources of the SSDT modification; see modification_sources.
- kernel_memory_hooks: (optional).
Type: List of the modified kernel memory areas; see below.
A list of the modified critical system areas.
- kernel_address: (optional).
Type: Hexadecimal number.
Example: 0x8056cdc0.
The modified kernel address.
- kernel_module_name: (optional).
Type: String.
Example: “c:\windows\system32\ntkrnlmp.exe”.
The modified kernel module name.
- area_name: (optional).
Type: String.
Example: “kernel image section PAGE”.
A name of the modified critical area.
- kernel_function_name: (optional).
Type: String.
Example: “NtCreateFile”.
A name of the modified system function.
- modification_sources: (optional).
Type: List of the sources of the kernel memory modification; see modification_sources.
- modification_sources: (optional).
Type: List of the sources of the code or memory modification.
- virtual_address: (optional).
Type: Hexadecimal number.
Example: 0xfffff880041f1b9d.
The virtual address of an instruction which overwrote an original code or memory.
- modifier_module_name: (optional).
Type: String.
Example: “c:\windows\system32\hellodrv.sys”.
The module containing the instruction which overwrote an original code or memory.
- service_creates: (optional).
Type: List of services. See below.
A list of the services created by the analysis subject.
- service_file: (optional).
Type: File. see file_reads.
- service_name: (optional).
Type: String.
A display name to be used by user interface programs to identify the service.
- start_type: (optional).
Type: Integer.
Example: 0x00000002 (SERVICE_FILE_SYSTEM_DRIVER)
The service type.
- start_type: (optional).
Type: Integer.
Example: 0x00000000 (SERVICE_BOOT_START)
The service start options.
- service_starts: (optional).
Type: List of services; see service_creates.
A list of services started by the analysis subject.
- service_stops: (optional).
Type: List of services; see service_creates.
A list of services stopped by the analysis subject.
- service_changes: (optional).
Type: List of services changes; see below.
A list of the services changed by the analysis subject.
- service_name: (optional).
Type: String.
Example: “WNKiserv”
A display name to be used by user interface programs to identify the service.
- change: (optional).
Type: String.
A change of the service made by the analysis subject.
- driver_loads: (optional).
Type: Services; see service_creates.
A list of the drives loaded by the analysis subject.
- driver_unloads: (optional).
Type: Services; see service_creates.
A list of the drives unloaded by the analysis subject.
- dns_queries: (optional).
Type: List of DNS queries; see DNS query.
List of DNS queries done by the analysis subject.
- network_connections: (optional).
Type: List of network connections; see network connection.
List of network connections done by the analysis subject using a protocol that is not parsed into a more specific protocol type.
- http_conversations: (optional).
Type: List of HTTP connections; see HTTP connection.
List of network connections identified to use the HTTP protocol done by the analysis subject.
- irc_conversations: (optional).
Type: List of IRC connections; see IRC connection.
List of network connections identified to use the IRC protocol done by the analysis subject.
- ftp_conversations: (optional).
Type: List of FTP connections; see FTP connection.
List of network connections identified to use the FTP protocol done by the analysis subject.
- smtp_conversations: (optional).
Type: List of SMTP connections; see SMTP connection.
List of network connections identified to use the SMTP protocol done by the analysis subject.
- address_scans: (optional).
Type: List of network address scans; see address scan.
List of network address scans done by the analysis subject.
- downloaded_files: (optional).
Type: List of file-download tuples; see below.
List of files that were downloaded using the Microsoft Windows file-download API functions. Each element is a tuple of file-origin URL and a File element (see file_reads).
Note: This list does not contain files downloaded using other mechanisms or protocol (such as HTTP). Those are listed in the corresponding network section.
- pe_images: (optional).
Type: List of PE images; see below.
A list of PE images found in the memory of the analysis subject.
- image.
Type: PE image; see Portable Executable Image.
Process image information extracted when included in the analysis.
- image_diff: (optional).
Type: PE image; see Portable Executable Image.
Process image information extracted at program termination or analysis end.
- memory_blocks: (optional).
Type: List of memory-blocks; see below.
A list of allocated memory regions found in the memory of the analysis subject.
- name: (optional).
Type: String.
Example: “mem_b67f3190f04083ac1e0189307f4d64d4”.
A name of the memory block. Format: mem_<md5>.
- size: (optional).
Type: Integer.
A size of the memory block in bytes.
- start_va: (optional).
Type: Integer.
A VA to where the memory block starts.
- end_va: (optional).
Type: Integer.
A VA to where the memory block ends.
- access: (optional).
Type: Hexadecimal string.
A set of flags that indicate the memory block’s attributes (such as code/data, readable, or writable).
- number_of_executed_pages: (optional).
Type: Integer.
A number of executed pages in the memory block.
- executed_pages: (optional).
Type: List of integers.
A list of VA of executed pages.
- dist_bytes_vector: (optional).
Type: Hexadecimal string.
An internal field used by an analysis engine.
- average_bytes: (optional).
Type: Hexadecimal string.
An internal field used by an analysis engine.
- autocorrelation: (optional).
Type: Floating-point number.
An autocorrelation of the memory block data.
- entropy: (optional).
Type: Floating-point number.
An entropy of the memory block data.
- embedded_pe_header.
Type: Boolean.
True if we recognized a PE image header in the memory block.
- number_of_strings: (optional).
Type: Integer.
A number of found strings in the memory block.
- strings: (optional).
Type: List of strings.
Example: “SSP3FR.DLL”,”ROOF\”,”Help Button”.
A list of strings found in the memory block.
- md5.
Type: Hexadecimal string.
A md5 hash of a content.
- strings_lists: (optional).
Type: List of named strings-lists; see below.
A list of named strings-lists. The name identifies a type of the strings in the list.
- name: (optional).
Type: String.
Example: “heap_strings”.
A name of the string list.
- strings: (optional).
Type: List of strings.
Example: “ProgramData=C:\ProgramData”,”NUMBER_OF_PROCESSORS=1”,”ncacn_ip_tcp”.
A list of strings.
- patched_sleeps: (optional).
Type: List of patched sleep values; see below.
A list of patched sleep values. It is an anti-evasion technique which changes a waiting period (if it is too long) for a sleep function and timers.
- count: (optional).
Type: Integer.
Example: 1.
A number of times the sleep function was called.
- new_value: (optional).
Type: Integer.
Example: 5.
A new value of the waiting period in seconds.
- old_value: (optional).
Type: Integer.
Example: 3600.
A old value of the waiting period in seconds.
- strings_comparisons: (optional).
Type: List of string comparisons; see below.
A list of string comparisons.
- name: (optional).
Type: String.
Example: “shlwapi.dll.StrStr_generic”.
A possible name of the string comparison function. Usually defined by a flirt signature flirt_signatures.
- src_string: (optional).
Type: String.
Example: “C:\Users\Public\Desktop”.
A comparable string 1.
- dst_string: (optional).
Type: String.
Example: “%SYSTEMROOT%”.
A comparable string 2.
- src_sources: (optional).
Type: List of strings.
Example: “\Registry\Machine\Software\Classes\.dot\Icon”,”Command line”.
A a list of possible sources (from where this string could be read) for string 1.
- dst_sources: (optional).
Type: List of strings.
Example: “\Registry\Machine\Software\Classes\.dot\Icon”,”Command line”.
A a list of possible sources (from where this string could be read) for string 2.
- frequent_api_calls: (optional).
Type: List of the frequent API calls; see below.
A list of the frequent API calls.
- name: (optional).
Type: String.
Example: “NtOpenThreadToken”.
A name of the API function which was frequently called.
- count: (optional).
Type: String.
Example: 31440.
A number of times the API function was called.
- pid: (optional).
Type: Integer.
Example: 145.
Windows process identifier (TID) of the calling process.
- tid: (optional).
Type: Integer.
Example: 167.
Windows thread identifier (TID) of the calling thread.
- yara_signatures: (optional).
Type: List of the Yara signatures; see below.
A list of the Yara signatures which hit on the analysis subject.
- name: (optional).
Type: String.
Example: “apt_win_generic_imageStego”.
A name of the Yara signatures.
- score: (optional).
Type: Integer.
Example: 75.
A score which defines how dangerous the analysis subject according to the Yara signature. Possible range from 0 (benign) to 100 (malicious).
- internal: (optional).
Type: Boolean.
If true the signature is only for an internal usage.
- flirt_signatures: (optional).
Type: List of the Yara signatures; see below.
A list of the flirt signatures which hit on the analysis subject. The flirt signatures recognize a known functions.
- name: (optional).
Type: String.
Example: “___ascii_strnicmp”
Name of the signature.
- keyboard_capture: (optional).
Type: List of keyboard actions captured; see below.
A list of keyboard actions sent during the analysis which were seen on malware behavior.
- word: (optional).
Type: String.
Example: “8989-8408-5161-4765”
Word captured by sample during analysis.
- word_type: (optional).
Type: String.
Example: “Credit Card”
Type of word that was captured.
Windows Process¶
Information on a Windows process.
Windows process contents
- process_id.
Type: String.
Example: “1376”.
Windows process identifier (PID).
- executable: (optional).
Type: File; see file_reads.
Process image information.
- arguments: (optional).
Type: String.
Example: “C:\subject.exe arg1 arg2”.
Full command line used to start the analysis subject.
- bitsize: (optional).
Type: Integer.
Example: 32.
Process bit-size (32bit or 64bit process).
- analysis_subject_id: (optional).
Type: Integer.
Example: 2.
Identifier of the analysis subject within the analysis report if the process belongs to an analysis subject monitored in the analysis run.
Portable Executable Image¶
A process image extracted during the analysis run.
Process image contents
- name: (optional).
Type: String.
Example: “pe_i_5177683cb94a34bfb52142cfb1c49806”.
A name of the section.
Format:
“main” for the main PE image in the process.
“pe_i_<md5>” for the unknown PE image in the process recognized as loaded image.
“pe_f_<md5>” for the unknown PE image in the process recognized as non-loaded image.
- image_base.
Type: Integer.
When the linker creates an executable, it assumes that the file will be memory-mapped to a specific location in memory.
- directories_mask.
Type: Binary string.
A bit mask which shows a presence of each entry in DataDirectory of the image.
- number_of_sections.
Type: Integer.
A number of sections in the image.
- average_bytes.
Type: Hexadecimal string.
An internal field used by an analysis engine.
- dll.
Type: Boolean.
true if the image is a Dynamic Load Library
- entry_point.
Type: Integer.
An address where the loader will begin execution.
- image_size.
Type: Integer.
A size of the region starting at the image base up to the end of the last section.
- loaded.
Type: Boolean.
True if we recognized an image as a loaded PE image. False if we recognize as image as a file. (non loaded PE image).
- md5.
Type: Hexadecimal string.
A md5 hash of a content.
- sections: (optional).
Type: List of sections; see below.
PE image sections.
- md5_phys: (optional).
Type: Hexadecimal string.
A md5 hash of physical data of the section (offset : offset + physical_size).
- md5_virt: (optional).
Type: Hexadecimal string.
A md5 hash of virtual data of the section (virtual_address : virtual_address + virtual_size).
- name: (optional).
Type: String.
Example: “.text”.
A name of the section.
- physical_size: (optional).
Type: Integer.
A size of the section after it’s been rounded up to the file alignment size.
- offset: (optional).
Type: Integer.
A file-based offset of where the raw data emitted by the compiler or assembler can be found.
- virtual_size: (optional).
Type: Integer.
A size of the section after it’s been rounded up to the page alignment size.
- virtual_address: (optional).
Type: Integer.
A RVA to where the loader should map the section.
- characteristics: (optional).
Type: Hexadecimal string.
A set of flags that indicate the section’s attributes (such as code/data, readable, or writable).
- dist_bytes_vector: (optional).
Type: Hexadecimal string.
An internal field used by an analysis engine.
- average_bytes: (optional).
Type: Hexadecimal string.
An internal field used by an analysis engine.
- autocorrelation: (optional).
Type: Floating-point number.
An autocorrelation of the section data.
- entropy: (optional).
Type: Floating-point number.
An entropy of the section data.
- number_of_strings: (optional).
Type: Integer.
A number of found strings in the section.
- strings: (optional).
Type: List of strings.
Example: “SSP3FR.DLL”,”ROOF\”,”Help Button”.
A list of strings found in the section.
Windows Analysis Metadata Format¶
During the analysis run, the analysis engine extracts the metadata that is available for download. This type extends the Analysis Metadata Format type.
Metadata contents
- file: (optional).
Type: File; see file_reads.
Name of the file generated during the analysis run. Applies to metadata_type “generated_file”.
Windows Analysis Process Dumps (PE Snapshots)¶
The analysis engine extracts process dumps/snapshots of the programs under analysis whenever an interesting action is triggered. These snapshots are exported via analysis metadata; see Windows Analysis Metadata Format.
These snapshots are available in two formats:
- process_snapshot:
This snapshot type is generated for all 32-bit or 64-bit processes that are tracked during the analysis. For each process, the process snapshot file contains allocated memory sections/areas mapped during the analysis, as well as metadata describing the placement of these different memory sections within the process memory and how the content/placement changes over time.
- process_dump: (deprecated).
For 32-bit processes, the system exports PE files which can be analyzed with a wide variety of tools. Since the PE format is limited to describing code/data sections loaded at 32-bit addresses, this snapshot type is not applicable to 64-bit processes or programs that load data beyond the 32-bit address range.
At the same time, this snapshot type does not support multiple snapshot states within one file, as supported by files in the process_snapshot format.
IDA Pro Integration¶
When loading a process_snapshot file in IDA Pro, the code is annotated with runtime information extracted during the dynamic analysis, such as API function exports, program entry-points, or instruction addresses of interesting code regions.
To get started, download the Python loader available at https://github.com/vmware-samples/process-snapshots-toolkit/blob/main/ida_scripts/process_snapshot_loader.py to the IDA Pro directory <IDA dir>/loaders/.
With the loader added to IDA Pro, the program offers a new loader window for process snapshots generated by the Lastline analysis system:
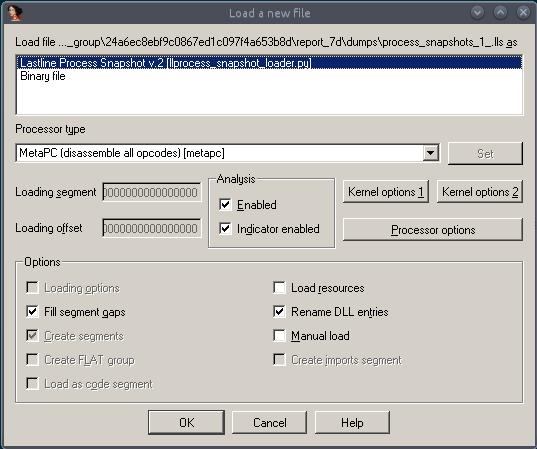
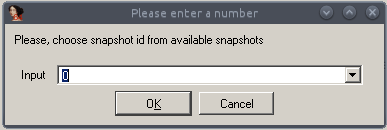
Select the Lastline Process Snapshot option. The IDA loader displays the snapshots available in the input file, as well as additional metadata for each individual snapshot; select the snapshot for analysis and confirm with OK.
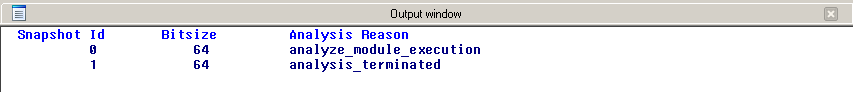
IDA Pro assembles the data and code blocks as they were placed within the process memory at the point of the snapshot, and annotates the code with all available metadata: functions referenced from untrusted code are colored in blue, otherwise grey:
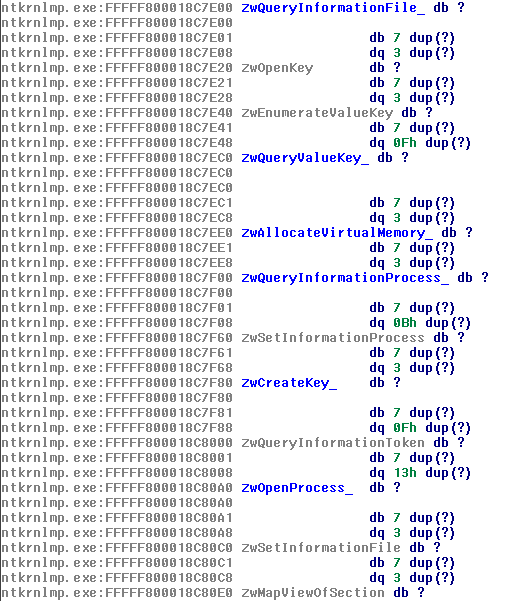
Loaded system modules are represented as empty segments with exported functions as named references:
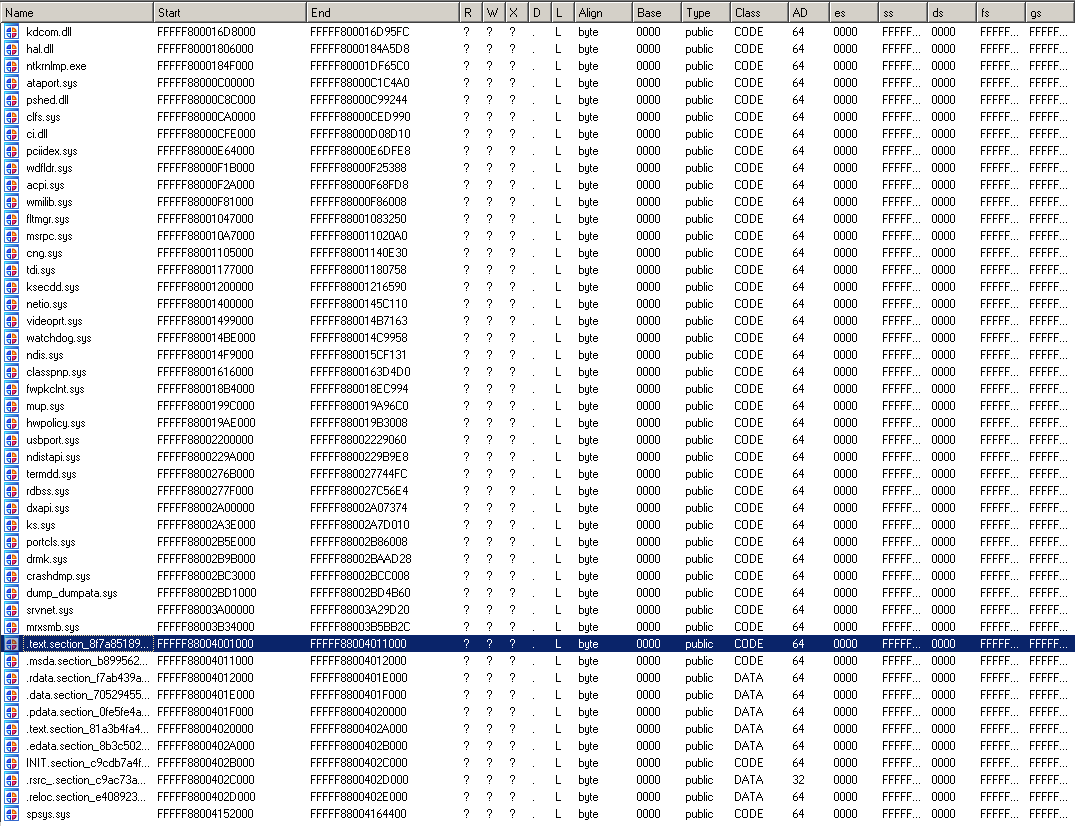
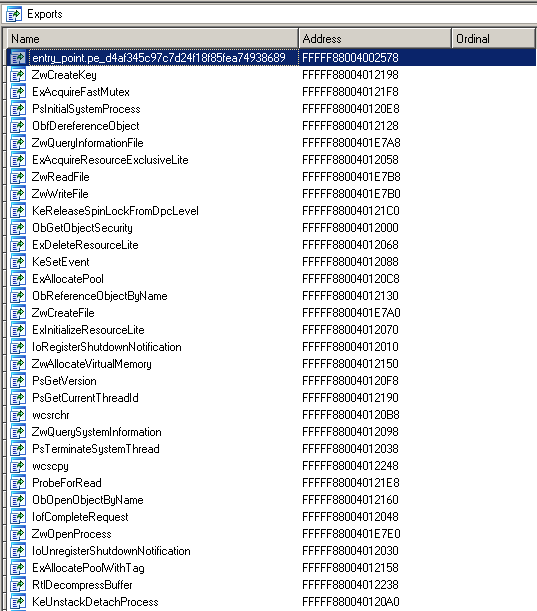
Unfortunately, IDA Pro currently does not provide the API to modify the program import table. As workaround, the loader exports a list of interesting entry points found by the analysis engine as well as references to API invocations from process memory as export table:
Unsupported IDA Pro Versions
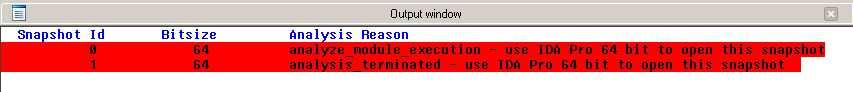
When opening a process snapshot using an unsupported version of IDA Pro, the following error message is displayed:
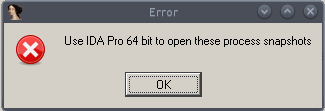
This can happen, for example, when a 64-bit process snapshot is opened in an IDA Pro version limited to the analysis of 32-bit programs.
Likewise, the list of unavailable snapshots for this version of IDA Pro are marked accordingly: